Managing Access with IP Whitelisting and Blacklisting
Requirements: CoreSSH Server
CoreSSH Server is an easy-to-use solution for managing the server-side of secure file transfer. This guide will focus on configuring IP whitelists and blacklists to control access to the server.
Address Rules
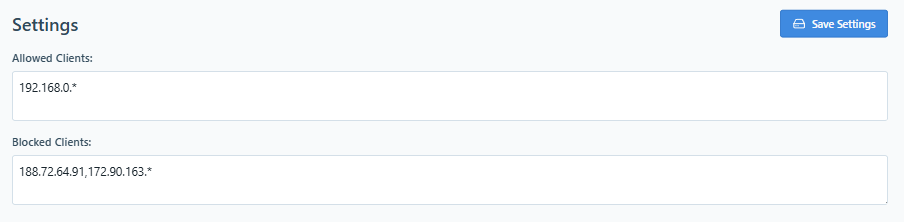
To restrict which clients can connect to CoreSSH Server, you can configure Allowed Clients and Blocked Clients settings. These options let you define rules that permit or deny connections based on the client's IP address.
These settings accept a comma-separated list of IP addresses or patterns, with support for wildcards (*) to match IP ranges.
Automated Blocking
In addition to manual IP access control, CoreSSH Server supports automatic blocking of IP addresses that repeatedly fail to authenticate. This mechanism helps defend against brute force attacks by automatically throttling suspicious traffic.
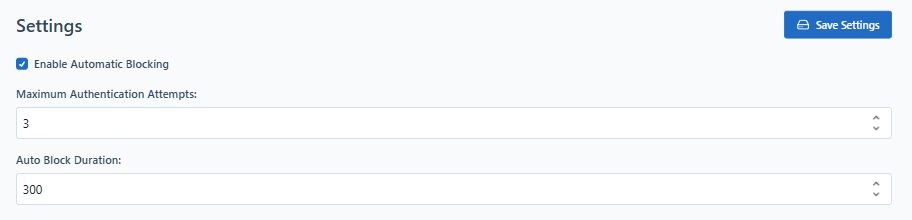
The Enable Automatic Blocking setting turns this on or off. Further specify the number of failed logins before the block is triggered in the Maximum Authentication Attempts setting. The length of time the client will be blocked (in seconds) in Auto Block Duration.
We appreciate your feedback. If you have any questions, comments, or suggestions about this article please contact our support team at support@nsoftware.com.

